Table of Contents
In today’s rapidly evolving digital landscape, selecting the appropriate network security solutions has become a critical strategic imperative for organizations across all industries.
With cybercrime costs projected to reach $10.5 trillion annually by 2025, implementing comprehensive network security system components, network security software, and network security services is essential for protecting organizational assets and maintaining business continuity.
The complexity of modern IT environments, including hybrid cloud infrastructures, remote workforces, and IoT device proliferation, has expanded attack surfaces exponentially.
This comprehensive guide provides organizations with the essential framework for evaluating and selecting network security solutions that align with their specific requirements, risk profiles, and operational objectives while ensuring scalable protection against emerging threats.
Why Network Security Matters in 2025
The cybersecurity threat landscape in 2025 presents unprecedented challenges that underscore the critical importance of robust network security system implementations.
Advanced Threat Evolution
- AI-driven threat acceleration: 37% of security professionals report complete strategy overhauls
- Machine learning exploitation: Automated vulnerability discovery and attack optimization
- Deepfake weaponization: Sophisticated social engineering campaigns
- AI-powered credential attacks: Traditional authentication compromise within minutes
Identity-Based Attack Proliferation
- Non-human account growth: Higher count of service accounts than people
- API key targeting: Primary focus for credential-based attacks
- Privileged access failures: 80% contribution to successful data breaches
- Credential stuffing surge: 200% year-over-year increase
Network Perimeter Dissolution
- Remote workforce expansion: Corporate networks in unsecured environments
- Cloud resource distribution: Confidential data residing on multiple external services
- IoT device proliferation: Thousands of potential network entry points
- Mobile device integration: Blurred personal and corporate data boundaries
The financial implications are substantial, with comprehensive network security services becoming essential as average data breach costs reach $4.88 million in 2024.
What Is a Network Security Solution?
Network security solutions encompass integrated combinations of hardware, software, and services designed to protect organizational networks from unauthorized access and sophisticated cyber threats.
These comprehensive systems establish multiple defensive layers that work synergistically to ensure complete network protection across all entry points and attack vectors.
Core Components
- Hardware platforms: Next-generation firewalls, and intrusion detection systems, network access controllers
- Software platforms: SIEM tools, endpoint protection, AI-powered detection engines, vulnerability management
- Service provisions: Managed security providers, penetration testing, incident response coordination
- Integration capabilities: Seamless connectivity with existing IT infrastructure and enterprise systems
These integrated components maintain fundamental security principles through sophisticated network security software while adapting to evolving threat landscapes.
Key Features to Look for in Network Security Solutions
Selecting effective network security solutions requires careful evaluation of features that address current threats while providing scalability for future requirements.
Essential Security Capabilities
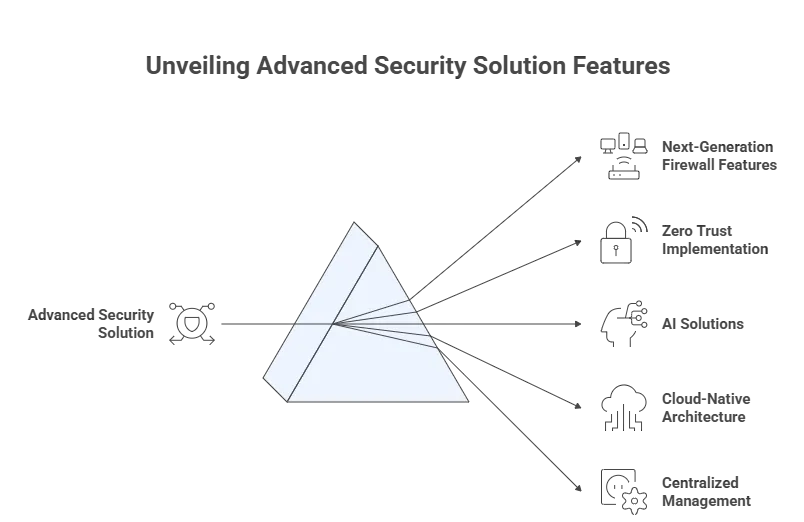
- Next-generation firewall features: Application-layer inspection, integrated intrusion prevention, advanced malware detection
- Zero trust implementation: Continuous verification protocols, micro-segmentation capabilities, dynamic access adjustment
- Artificial intelligence solutions: Machine learning models, advanced anomaly detection, predictive threat intelligence
- Cloud-native architecture: API-first design, container security monitoring, multi-cloud visibility
- Centralized management: Unified dashboard interface, real-time monitoring, customizable reporting functionality
Scalability Considerations
- Flexible architecture support: Small business to enterprise deployment scaling
- Modular architecture strategy: Incremental capability addition as requirements evolve
- Automated update delivery: Continuous emerging threat protection systems
- Performance optimization: Network infrastructure expansion effectiveness maintenance
How to Evaluate Your Organization’s Security Needs
Effective network security system selection requires systematic assessment of organizational requirements, risk factors, and operational constraints.
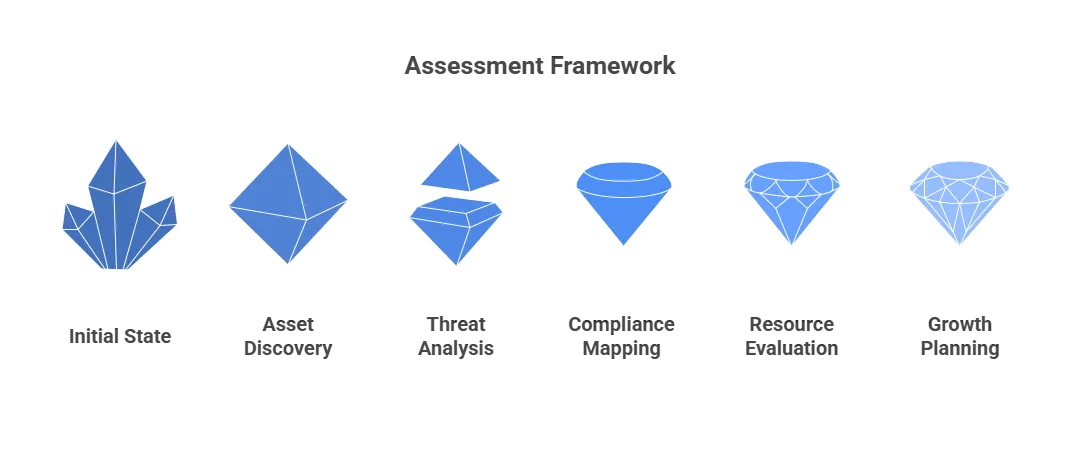
Assessment Framework
- Asset discovery process: Network-connected device inventory, application cataloging, critical pathway mapping
- Threat analysis: Industry-specific research, historical incident analysis, insider threat assessment
- Compliance mapping: Applicable regulation identification, security control documentation, compliance gap assessment
- Resource evaluation: Internal security expertise, team capacity, total ownership calculation
- Growth planning: Technology adoption evaluation, threat landscape evolution, emerging technology integration
This structured approach through comprehensive network security services analysis ensures organizations select appropriate solutions for their specific needs.
Top Network Security Solutions in 2025
The network security solutions market in 2025 is characterized by AI-driven capabilities, cloud-native architectures, and integrated threat intelligence platforms.
Leading Solution Categories
- AI-enhanced platforms: Predictive threat detection, automated incident response, behavioral pattern recognition
- Zero trust architecture: Distributed workforce management, granular access controls, attack surface reduction
- Extended detection platforms: Security data integration, holistic threat visibility, coordinated response mechanisms
- Cloud security management: Configuration visibility, compliance monitoring automation, automated remediation
- Managed security services: 24/7 monitoring capabilities, threat hunting expertise, cost-effective maintenance
Selection Priorities
- Integration capabilities: Existing infrastructure compatibility and third-party tool support
- Scalability features: Future growth accommodation and technology evolution adaptation
- Vendor reliability: Proven track record and comprehensive support services
- Cost effectiveness: Total ownership evaluation and ROI demonstration
Implementation Best Practices
Successful deployment of network security software requires careful planning and structured implementation approaches.
Implementation Steps
- Phased deployment: Gradual rollout to minimize business disruption
- Staff training: Comprehensive user education and technical skill development
- Testing protocols: Security validation and performance optimization
- Monitoring infrastructure: Continuous threat detection and incident response preparation
Ongoing Management
- Regular updates: Security patch management and feature enhancement deployment
- Performance monitoring: System optimization and capacity planning
- Compliance verification: Regulatory requirement adherence and audit preparation
- Incident response: Breach containment procedures and recovery planning
Conclusion
Selecting appropriate network security solutions represents a critical strategic decision that directly impacts organizational resilience and business continuity. With increasingly sophisticated AI-driven attacks, organizations cannot afford inadequate security measures.
Success requires comprehensive organizational requirement understanding, systematic solution evaluation, and scalable system selection. Organizations should invest in layered defense strategies combining advanced technology with comprehensive employee training through professional network security services.
The investment in robust security today will determine organizational resilience and competitive advantage in tomorrow’s threat landscape.
FAQ
Which network security solution is most critical for businesses?
Next-generation firewalls represent the most critical network security system components, serving as primary defense mechanisms with application-layer inspection, intrusion prevention, and intelligent threat filtering capabilities.
What are the main types of network security?
The fundamental types include Network Access Control (NAC), Firewalls, Intrusion Detection Systems (IDS/IPS), Virtual Private Networks (VPNs), and Antivirus solutions working within comprehensive security frameworks.
How do you evaluate network security needs?
Evaluation involves asset discovery, threat analysis, compliance mapping, resource assessment, and growth planning to ensure selected solutions align with organizational requirements and risk profiles.