Table of Contents
In today’s digital age, where businesses and individuals rely heavily on networks to connect and share information, safeguarding these networks from cyber threats has become paramount.
Network security solutions play a crucial role in protecting networks from various attacks, such as unauthorized access, malware, and data breaches.
By understanding the different types of network security solutions and their key features, organizations can make informed decisions to bolster their network security posture.
Defining Network Security Solutions
Network security solutions are specialized hardware devices designed to protect networks from cyber threats.
These appliances are deployed at strategic points within a network to monitor and control network traffic, identify potential threats, and take appropriate actions to prevent attacks.
By acting as a barrier between a network and the internet and network security solutions help to safeguard sensitive data and ensure business continuity.
The Importance of Network Security Solutions in Today’s Digital Landscape
The need for robust network security solutions has never been greater.
As businesses increasingly adopt cloud-based services, remote work, and the Internet of Things (IoT), their attack surface expands significantly.
Cybercriminals are constantly evolving their tactics and exploiting vulnerabilities to gain unauthorized access to sensitive data and database software environments.
Network security appliances provide a critical line of defense by detecting and preventing a wide range of cyber threats, and protecting organizations from financial losses, reputational damage, and operational disruptions. For remote teams and individual users, adding a reliable VPN service can further enhance privacy by encrypting internet traffic and reducing exposure to network-based threats.
They also play a vital role in supporting PCI DSS compliance services, ensuring that businesses handling payment data adhere to strict security standards and safeguard customer information.
Types of Network Security Solution Appliances
When it comes to network security management, you need to strong network.
These are the types of network security products are available, each with specific functions and capabilities.
Let’s explore some of the most common types:
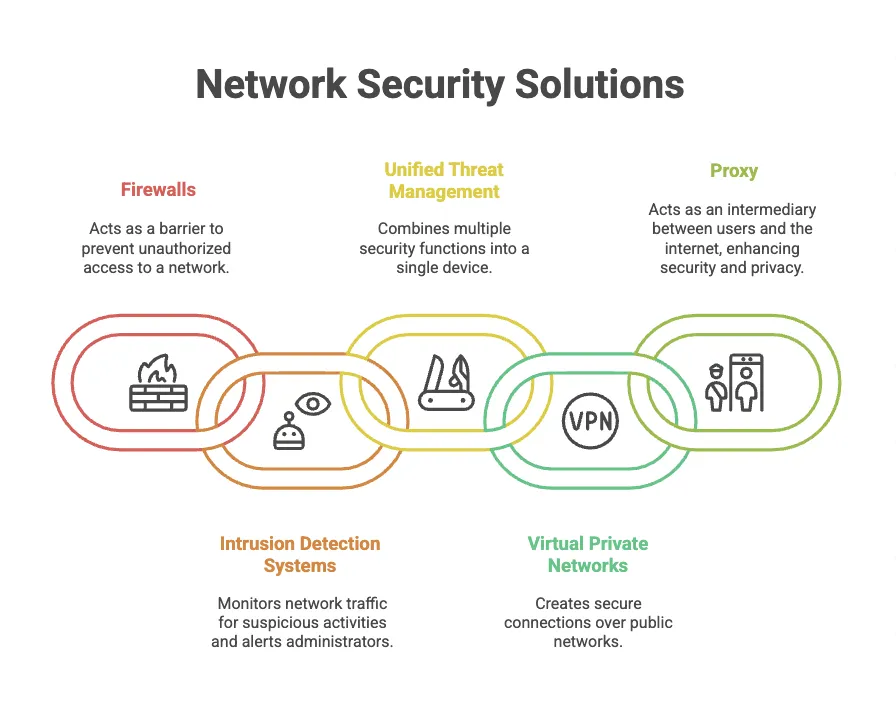
1. Firewalls
Firewalls are among the most fundamental network security appliances.
They act as gatekeepers, controlling traffic flow between a network and the internet.
Firewalls examine network traffic for suspicious activity, such as unauthorized access attempts or malicious code.
They can be configured to block or allow traffic based on specific criteria, such as IP addresses, ports, and protocols.
2. Intrusion Detection and Prevention Systems (IDPS)
IDPS systems are designed to detect and prevent unauthorized access to networks.
They continuously monitor network traffic for signs of intrusion, such as abnormal patterns of activity or known attack signatures.
If an intrusion is detected, IDPS systems can take immediate action to block the attack and alert administrators.
3. Unified Threat Management (UTM) Devices
UTM devices combine multiple security functions into a single appliance, providing comprehensive protection against a wide range of threats.
These devices typically include features such as firewall, intrusion prevention, antivirus, content filtering, and VPN capabilities.
UTMs offer a cost-effective solution for organizations that need to protect their networks from various threats.
4. Virtual Private Network (VPN) Appliances
Business VPNs create secure, encrypted tunnels between networks, allowing users to connect remotely to a corporate network and access resources securely.
VPNs are commonly used for remote access, telecommuting, and branch office connectivity.
They help to protect sensitive data transmitted over the internet by encrypting it and preventing unauthorized access.
They can be extremely useful for businesses that leverage international PEO and work with a global team across various locations.
Vpn Vs Proxy
VPN – It’s a virtual private network that encrypts all your internet traffic and send it through a secured server.
It works at the system level meaning all apps and browsers on your device are covered. With VPN you will expect privacy, security, and accessing geo blocked content.
Proxy – Unlike VPN, it routes traffic from a specific app or web browser. It hides your IP address but doesn’t encrypt your data, which makes it less secure than a VPN. A proxy server can manage this traffic efficiently, and if you’re unsure whether your proxy is working correctly or what type it is, you can use a proxy checker tool to verify its performance and anonymity level.
Next-Generation Firewalls (NGFW)
NGFWs are advanced firewalls that provide additional security features over traditional firewalls.
They can inspect traffic at the application layer, providing more granular control over network access.
NGFWs also incorporate features such as intrusion prevention, malware detection, and application control to provide comprehensive protection against sophisticated threats.
Endpoint protection
Endpoint security protects devices like laptops, phones, and servers from cyber threats.
With more remote work and personal devices in use, each device becomes a potential risk.
Modern endpoint protection uses tools like antivirus, firewalls, and AI-powered threat detection to secure these endpoints.
It also allows centralized monitoring and quick responses to attacks.
This security is essential for protecting data, staying compliant, and keeping operations running smoothly.
Key Features to Consider
When selecting network security appliances, it is important to consider several key features:
- Performance and Throughput: The appliance should be able to handle the expected network traffic without compromising performance. Look for appliances with high throughput capabilities to ensure smooth network operations.
- Scalability: As your network grows, the appliance should be able to scale to meet your changing needs. Consider appliances that can be easily expanded or upgraded to accommodate future requirements.
- User-Friendly Interface: A user-friendly interface makes it easier to manage and configure the appliance.
Look for appliances with intuitive dashboards and easy-to-use management tools. - Support for Multiple Protocols: The appliance should support a wide range of protocols, including HTTP, HTTPS, FTP, SMTP, and others. This ensures that it can protect your network from threats that may exploit different protocols.
- Reporting and Analytics Capabilities: Robust reporting and analytics features allow you to monitor network activity, identify potential threats, and track security trends.
Look for appliances that provide detailed reports and customizable dashboards.
Top Network Security Solutions Appliance Brands
Several leading vendors offer a wide range of network security solution appliances to meet the diverse needs of organizations.
Here are some of the top brands:
Cisco

Cisco is a well-known name in the list of networking security products, offering a comprehensive portfolio of network security appliances.
Their products include firewalls, intrusion prevention systems, VPN solutions, and unified threat management devices.
Cisco’s appliances are known for their reliability, performance, and ease of management.
With cisco you will have comprehensive network security monitoring tools that will provide you ultimate edge over others.
Fortinet

Fortinet is another leading provider of network security solutions.
Their products are designed to deliver high-performance, integrated security.
Fortinet offers a wide range of appliances, including firewalls, intrusion prevention systems, and unified threat management devices.
They are known for their innovative security technologies and strong focus on performance.
Palo Alto Networks

Palo Alto Networks is a cybersecurity company that specializes in next-generation firewalls and threat prevention solutions.
Their products are designed to provide advanced threat protection and visibility into network traffic.
Palo Alto Networks is known for its innovative approach to security and its ability to detect and prevent sophisticated attacks.
Sophos

Sophos offers a comprehensive suite of network security solutions, including firewalls, intrusion prevention systems, and endpoint protection.
Their products are known for their ease of use and effective threat protection.
Sophos also provides cloud-based security solutions for organizations that need to protect their cloud infrastructure.
Check Point

Check Point is a global leader in cyber security solutions, offering a wide range of products to protect networks, data centers, and cloud environments.
Their products include firewalls, intrusion prevention systems, VPN solutions, and unified threat management devices.
Check Point is known for its advanced security technologies and its commitment to innovation.
Although Check Point is counted as one of the successful network security technologies and solutions till date.
Comparison of Leading Appliances
To help you choose the right network security appliance for your organization, here is a comparison of some of the leading brands based on key features.
| Feature | Cisco | Fortinet | Palo Alto Networks | Sophos | Check Point |
| Performance | Excellent | Excellent | Excellent | Good | Excellent |
| Scalability | Good | Excellent | Excellent | Good | Excellent |
| User-friendliness | Good | Good | Excellent | Excellent | Good |
| Protocol support | Excellent | Excellent | Excellent | Good | Excellent |
| Reporting and analytics | Good | Excellent | Excellent | Good | Excellent |
| Pricing | Mid-range | Mid-range | Premium | Mid-range | Premium |
Difference Between Network Security Devices And Cyber Security Devices
The digital world is increasing with cyber threats and for that business must deploy right tools to protect their digital data.
While network security devices and cyber security devices are used interchangeably but they serve a whole different purpose altogether.
Now, let’s understand the major differeneces between the two.
What are Network Security Devices?
Network security devices are primarily consists of hardware and software that protects, monitor and manage the network traffic and infrastructure.
This helps in prevent unauthorised access, ensure safe data transmission, and maintain uptime.
Here are some common Network Security Devices:
- Firewalls – Monitor and filter incoming/outgoing traffic based on pre set rules.
- Intrusion Detection Systems (IDS) – Easily detect and alert on suspicious traffic or attacks
- Intrusion Prevention Systems (IPS) – You can actively block identified threats in real time.
- Network Access Control (NAC) – Regulates access based on compliance and identity
- Virtual Private Network Gateways (VPN) – Encrypt remote access for secure communications
What Are Cyber Security Devices?
Cyber security devices, on the other hand, provide protection on a broader scale.
This also comes with different tools that secure endpoints, software, user identities, cloud data, and digital assets from cyber threats like phishing, malware, ransomware, and insider attacks.
Here are some common Cyber Security Devices:
- Endpoint Detection And Response (EDR) – Monitors end user devices like laptops and servers
- Antivirus/Antimalware protection – Detects and removes malicious programs
- Data Loss Prevention (DLP) – You can easily stop sensitive data from being leaked or misused.
- Identity And Access Management (IAM) – identity and access management controls who can access what based on multiple roles.
- Cloud Security Posture Management (CSPM) – This helps secure cloud configurations and compliance.
Why You Need Both Of Them?
Your digital environment needs to be fully secured, that’s why you can’t solely depends on one type.
While network security devices defend the perimeter whereas cyber security devices protect the internal systems, users and data.
A layered security architecture combining both provides
- Real time intrusion prevention
- Device level protection
- Strong access control
- Safe cloud and remote access
- Enhanced incident response
How To Do Network Security Monitoring?
To ensure effective network security, it is important to follow the best practices for implementing and managing network security appliances
You can monitor network security through these points:
- Assessing Organizational Needs: Conduct a thorough assessment of your organization’s security needs to identify the appropriate types and features of network security products.
Consider factors such as network size, traffic volume, and the types of threats you face. To emphasize the risks of skipping this step, Dmitry Kurskov, cybersecurity consultant at ScienceSoft, warns: “If you neglect proper vulnerability assessment for longer than a year, you are likely to become an easy target for hackers.” This underscores the importance of proactive and recurring evaluation of your network infrastructure especially after any major changes. - Regular Updates and Maintenance: Keep your network security appliances up-to-date with the latest software and security patches. This also includes tracking whether your Fortinet devices are still supported, and using a reliable fortinet eol list helps teams quickly identify which appliances should be upgraded or replaced before they become a security risk.
Regular maintenance is essential to ensure optimal performance and protection against emerging threats. - Employee Training and Awareness: Educate your employees about the importance of network security equipments and how to recognize and avoid potential threats. For IT teams and aspiring professionals, formal training through a hands-on Network Engineer Course ensures deeper understanding of monitoring tools, incident response workflows, and enterprise-grade security practices.
Provide training on best practices for using the network and handling sensitive information. This can also include sharing social networking safety tips for businesses, helping employees understand how to maintain professionalism and data security on social media platforms. - Continuous Monitoring and Improvement: Monitor network activity regularly to identify potential security breaches or anomalies.
Continuously evaluate your security measures and adjust as needed to improve your organization’s security posture. To strengthen visibility across identity-based threats and prevent privilege abuse during network incidents, many organizations now integrate identity first incident response into their monitoring strategy—linking network activity with real-time identity context for faster, smarter containment.
Conclusion
Network security appliances are essential tools for protecting networks from cyber threats.
By understanding the different types of appliances, their key features, and best practices for implementation, organizations can make informed decisions to enhance their network security posture.
By understaning the importance of network security you can enhance your network security assessment that will protect you from varioud cyber threats.
By investing in robust network security, businesses can safeguard their sensitive data, protect their reputation, and ensure business continuity in today’s digital landscape.
Comment below your thoughts.
FAQ
1. What are the network security technologies and solutions?
Network security solutions are a combination of tools and technologies designed to protect an organization’s IT infrastructure from cyber threats and data breaches. These solutions includes network security products and network security appliances.
It also includes firewalls, intrusion detection and prevention systems, VPN Gateways, web and email security gateways.
2. What are the five types of network security?
Here are the five types of network security and each play a vital role in protecting data, and users from cyber threat. These layers often rely on a range of cyber security devices to ensure detailed protection.
Here are some of the key types Firewall security, intrusion prevention systems (IPS), Virtual private network (VPN), Antivirus and and anti malware protection, Access control and authentication.
3. What is the most common network security?
The most famous network security is firewall. It acts as a barrier between internal networks and external threats by monitoring and controlling traffic based on security rules.
Firewalls are one of the most important network security equipments and it is helpful for business of all sizes to prevent unauthorized access and filer malicious data.
4. What is the difference between network security and cyber security?
Network security focuses on protecting the integrity and usability of a company’s internal network using various tools like firewall, intrusion prevention systems and other network security technologies.
Cyber security is bit different because it’s broader terms and not only protecting networks, but also devices, data, applications and systems from digital attack.
5. What are the technologies used in Network Security?
It relies on a set of technologies and cyber security devices to protect all data from cyber threats.
The key technologies used here are Firewall, Intrusion detection and prevention systems, VPNs, Anti virus and anti malware, Network Access control, Security gateway.
These cyber security devices work together to create a layered defense strategy.