Table of Contents
The digital age has brought incredible convenience and fostered innovation, but it has also opened doors for cybercriminals. Ransomware attacks are now a major danger for both companies and people. These malicious software programs hold your data hostage, encrypting it and demanding a ransom payment for its decryption.
In this blog post, we’ll delve into the evolving tactics of ransomware attacks and equip you with effective mitigation strategies to protect yourself. Understanding these ever-changing threats is crucial to fortifying defenses and safeguarding valuable data.
Importance of Understanding Evolving Tactics
Ransomware attacks are constantly evolving, with cybercriminals adopting new techniques to bypass existing security measures. According to a report by Cybersecurity Insiders, ransomware attacks increased by 84% in 2022 compared to the previous year. This alarming statistic highlights the urgency for organizations and individuals to stay informed about the latest tactics employed by these attackers.
By understanding these tactics, you can proactively implement defense mechanisms that can deter attacks, minimize damage, and ensure a faster recovery process in case of a breach.
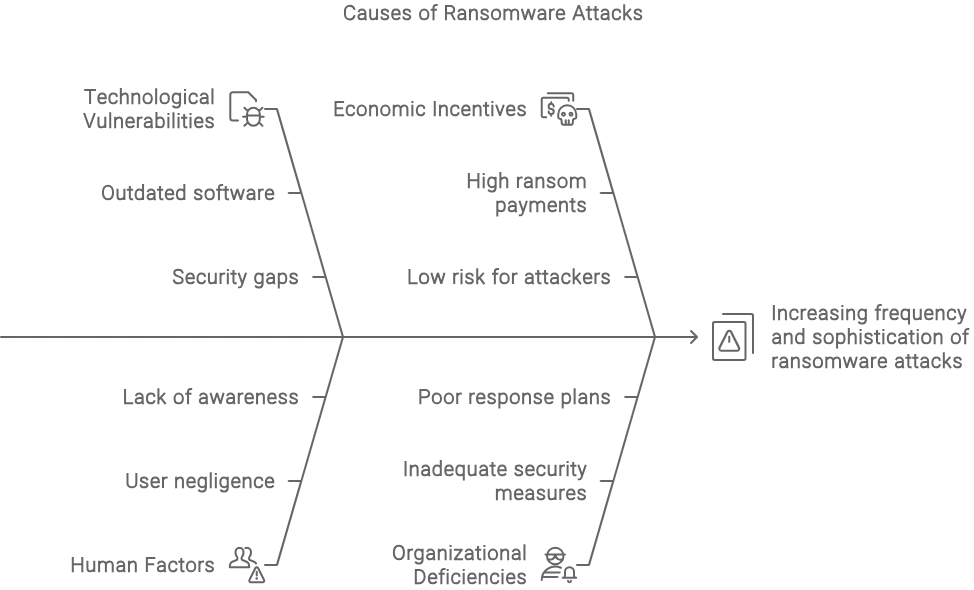
Current Trends in Ransomware Tactics
Let’s explore some of the most concerning trends in ransomware attacks:
- Increase in Double Extortion Schemes: Gone are the days when attackers solely relied on encryption. Today’s ransomware often employs a double extortion strategy. Hackers steal sensitive data before encrypting it, threatening to leak the information publicly if the ransom isn’t paid. This double threat puts immense pressure on victims, making them more likely to submit to the ransom demands.
- Targeting of Critical Infrastructure: The focus isn’t just on financial gain. In recent years, we’ve seen a rise in ransomware attacks targeting critical infrastructure like power grids, transportation systems, and healthcare providers. These attacks can have devastating consequences, disrupting essential services and impacting public safety.
- Use of Ransomware-as-a-Service (RaaS): Cybercrime has become an “as-a-service” industry. Ransomware-as-a-service (RaaS) operates through a model where technical expertise is no longer a barrier to entry. Criminals with limited technical skills can purchase access to ransomware tools and infrastructure from RaaS providers, making these attacks more widespread.
- Sophistication in Phishing Attacks: Phishing emails remain a primary method for delivering ransomware payloads. Attackers have become incredibly adept at crafting emails that mimic legitimate sources, tricking users into clicking on malicious links or opening infected attachments.
These are just a few examples, and new tactics are constantly emerging. Staying informed about the latest trends in ransomware attacks is critical for crafting an effective defense strategy.
Case Studies of Recent Ransomware Attacks
Looking at real-world examples can help illustrate the impact of these evolving tactics:
The Colonial Pipeline Attack
The Colonial Pipeline is a massive pipeline system in the United States that transports gasoline, diesel, and jet fuel from the Gulf Coast to the East Coast. In May 2021, it suffered a crippling ransomware attack orchestrated by a Russian hacking group called DarkSide.
This attack was particularly damaging because it disrupted the flow of fuel to a large part of the country. Gas stations ran dry, prices soared, and there was widespread panic. What made this attack even more alarming was the use of a “double extortion” tactic. The hackers not only encrypted the company’s data but also stole it, threatening to release sensitive information publicly if a ransom wasn’t paid.
This incident starkly highlighted the vulnerability of critical infrastructure to cyberattacks. It showed that even essential services like fuel transportation can be severely impacted by ransomware attacks, causing widespread economic and social disruption.

The JBS Attack
JBS is a global meat processing company, and when a ransomware attack hit it in May 2021, the repercussions were felt worldwide. The attack forced the company to shut down several of its plants, leading to meat shortages and price increases.
Similar to the Colonial Pipeline attack, the JBS incident underscored the economic power of ransomware. It demonstrated how a cyberattack on a single company can have a ripple effect, impacting entire industries and consumers. The attack also emphasized the need for robust cybersecurity measures in the food supply chain, a sector that is critical to global food security.
Both these attacks serve as stark reminders of the growing threat of ransomware and the importance of investing in strong cybersecurity defenses to protect critical infrastructure and essential services.
These are just two examples of high-profile ransomware attacks with significant consequences. By understanding the tactics used in these attacks and their impact, we can develop more robust defense strategies for the future.
Related Article: Cyber Threats in 2024: Navigating the Deepfake Dilemma
Ransomware attacks continue to escalate in 2024, with several key metrics highlighting the growing threat:
- Increase in Ransom Payments: The average ransom payment surged to over $1.54 million in 2023, nearly doubling from the previous year. Cybercriminals secured more than $1 billion in cryptocurrency payments due to ransomware activities.
- Success Rate of Attacks: An alarming 83% of organizations targeted by ransomware were attacked multiple times, with many companies opting to pay the ransom despite the risks. Notably, 35% of paid victims did not receive functional decryption keys.
- Industry Impact: The healthcare sector remains a prime target, leading critical infrastructure sectors with 249 reported ransomware cases in 2023. Supply chain attacks and new, more sophisticated attack methods are rising, targeting industries like manufacturing, IT, and government services.
- Global Trends: The first half of 2023 saw a 50% increase in ransomware attacks compared to the previous year, with a significant spike in incidents during Q2 and Q3 alone. This trend reflects the increasing frequency and sophistication of ransomware operations globally.
Healthcare: A Prime Target
The healthcare industry has become a particularly lucrative target for ransomware attackers. Here’s a breakdown of the staggering impact:
- From 2020 to 2025, healthcare will spend $125 billion to defend against breaches. (Chief Healthcare Executive, 2023)
- An average of 64.8 percent of healthcare data was restored after paying the ransom. (Health and Human Services, 2022)
- In the third quarter of 2022, one out of every 42 healthcare organizations faced ransomware attacks. Hospitals were the main targets, making up 74 percent of these attacks, while 26 percent were directed at other facilities like dental offices and nursing homes. (Check Point, 2022)
- Ransomware attacks on healthcare organizations increased twofold between 2016 and 2021. (Health and Human Services, 2022)
- For the 13th year in a row, the healthcare industry reported the most expensive data breaches, costing an average of $10.93 million. (IBM, 2023)
- In 2020, 80 ransomware attacks impacted 560 healthcare facilities. (Emsisoft, 2021)
These statistics underscore the critical need for robust cybersecurity measures in the healthcare industry.
Effective Mitigation Strategies
Now that you’re familiar with the evolving tactics, let’s explore strategies to mitigate ransomware threats:
Proactive Measures:
- Regular software updates and patch management: Outdated software contains vulnerabilities that attackers can exploit. Make sure to patch your operating systems and applications regularly to eliminate these vulnerabilities and close potential entry points for ransomware.
- Employee Training and Awareness Programs: Educate your employees about social engineering tactics used in phishing emails. Regular training programs can help them identify suspicious emails and avoid clicking on malicious links or attachments.
- Data Backup Solutions: Regularly back up your data to a secure, off-site location. In the event of a ransomware attack, having a recent backup can help you restore your data without paying a ransom.
Incident Response Planning:
- Importance of Having a Response Team: Establish an incident response team responsible for handling a ransomware attack. This team should have clear roles and responsibilities, including containment, eradication, recovery, and communication. Frequent practice drills can make sure the team is ready to react properly during a real attack.
- Steps in an Effective Incident Response Plan: A well-defined incident response plan outlines the steps to be taken during a ransomware attack. This includes isolating infected systems, containing the attack, investigating the incident, recovering data, and communicating with stakeholders.
- Communication Strategies During an Attack: Effective communication is crucial during a ransomware attack. Develop clear communication channels with employees, customers, and partners. Provide regular updates about the incident, its impact, and the steps being taken to address it. Transparency builds trust and can mitigate negative consequences.
Technological Solutions:
- Role of Firewalls and Intrusion Detection Systems: Firewalls act as the first line of defense, blocking unauthorized access to your network. Intrusion detection systems (IDS) monitor network traffic for suspicious activity, alerting you to potential threats. These technologies can help prevent ransomware from entering your system.
- Implementing Endpoint Detection and Response (EDR): EDR solutions provide visibility and control over endpoints, such as computers and mobile devices. They can detect and respond to threats before they spread, minimizing the impact of a ransomware attack. Organizations that lack 24/7 in-house expertise often supplement EDR with managed detection and response (MDR) services, such as a comprehensive MDR solution for MSPs by Acronis, which offers continuous monitoring, threat hunting, and rapid response.
- Use of Encryption and Access Controls: Encrypting sensitive data adds an extra layer of protection. Implementing strong access controls, such as multi-factor authentication (MFA), limits unauthorized access to your systems and data.
Conclusion
Ransomware attacks are a persistent and evolving threat that poses significant risks to organizations and individuals. Understanding the latest tactics employed by cybercriminals is essential for developing effective mitigation strategies. By combining proactive measures, incident response planning, and technological solutions, you can significantly reduce the risk of falling victim to ransomware.
Remember, prevention is always better than cure. Invest in robust cybersecurity measures, educate your employees, and stay informed about the evolving threat landscape. By prioritizing cybersecurity, you can protect your data, minimize disruptions, and build resilience against ransomware attacks.
In today’s digital world, safeguarding your data is paramount. Don’t become a victim. Take action now to protect your organization from the devastating consequences of a ransomware attack.