Table of Contents
OAuth 2.0
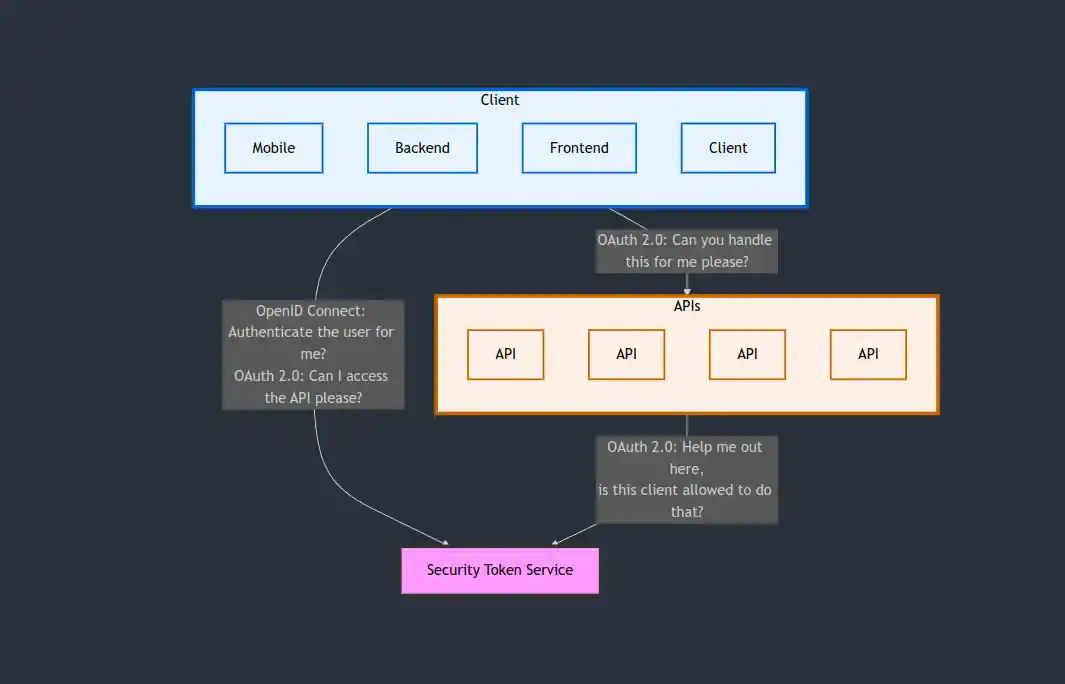
OAuth 2.0 is an authorization framework that allows applications to obtain limited access to user accounts on an HTTP service. It enables end-users to authorize third-party access to their server resources without sharing their credentials.
Key Concepts
- Roles:
- Resource Owner: The user who possesses the protected resources.
- Client: The application requesting access to resources.
- Resource Server: The server that holds the protected resources.
- Authorization Server: The server is issuing access tokens to clients.
- Tokens:
- Access Token: Access to protected resources requires specific credentials.
- Refresh Token: Credentials used to obtain new access tokens.
- Scopes:
- Define the specific access rights requested by the client.
- Flows:
- Different authorization flows for various use cases.
Authorization Grant Types
- Authorization Code Grant:
- Used by web and mobile apps.
- Involves two steps: getting an authorization code and exchanging it for an access token.
- Implicit Grant:
- Simplified flow for client-side apps.
- An access token is returned immediately without an intermediate authorization code.
- Resource Owner Password Credentials Grant:
- Used when the resource owner trusts the client with their credentials.
- The client directly handles the resource owner’s credentials.
- Client Credentials Grant:
- Used for client-to-client authentication.
- No resource owner involvement.
Security Considerations
- Use of HTTPS for all OAuth 2.0 interactions.
- Proper validation of redirect URIs.
- Short-lived access tokens.
- Secure storage of client secrets and tokens.
OpenID Connect (OIDC)
OpenID Connect is an identity layer built on top of OAuth 2.0, adding authentication capabilities to the authorization framework.
Key Concepts
- ID Token: A JSON Web Token (JWT) containing claims about the authentication event and user.
- UserInfo Endpoint: An API that retrieves claims about the authenticated user.
- Standard Claims: Predefined user attributes like ‘sub’ (subject identifier), ‘name’, ’email’, etc.
- Scopes: Specific OIDC scopes like ‘openid’, ‘profile’, and ’email’.
Flows
- Authorization Code Flow:
- Similar to OAuth 2.0’s Authorization Code Grant.
- Returns an ID Token along with the access token.
- Implicit Flow:
- Similar to OAuth 2.0’s Implicit Grant.
- Returns the ID Token and access token directly to the client.
- Hybrid Flow:
- It combines elements of both authorization code and implicit flows.
Features
- Discovery: /.well-known/openid-configuration endpoint provides server metadata.
- Dynamic Client Registration: Allows clients to register with the Authorization Server dynamically.
- Session Management: Provides mechanisms for managing login sessions.
- Front-Channel Logout: Allows logout through the browser without direct back-channel communication.
Security Considerations
- Proper validation of ID Tokens.
- Use of nonce values to prevent replay attacks.
- Implementation of PKCE (Proof Key for Code Exchange) for public clients.
| OAuth 2.0 | OpenID Connect (OIDC) |
| Focuses on authorization—delegating access to resources. | Focuses on authentication—verifying user identity. |
| Does not provide user identity details (it only issues access tokens for resources). | Provides user identity information via ID Tokens and optional UserInfo endpoint. |
| Primarily used to control access to APIs and data. | Used to authenticate users in applications (e.g., login systems). |
| Can be used alone or integrated with other protocols like SAML. | Built directly on top of OAuth 2.0, adding identity verification. |
| Authorization grants are exchanged for access tokens. | Authorization grants are exchanged for both access tokens and ID tokens. |
| Widely used for API access, resource sharing, and delegation between applications. | Popular for Single Sign-On (SSO) systems and identity federation. |
Use Cases
- OAuth 2.0 is typically used when an application needs to access user data (such as Google Drive files) without needing the user’s password.
- OIDC is ideal for implementing user authentication in applications where identity verification is required, such as logging into web applications via third-party providers (e.g., “Login with Google”).
Conclusion
By combining OAuth 2.0’s robust authorization capabilities with standardized authentication mechanisms, OpenID Connect provides a comprehensive solution for modern identity and access management needs. This dual approach ensures secure delegation of user resource access while confirming user identity in a trusted manner.
With support for Single Sign-On (SSO) and identity federation, OIDC streamlines user experiences across platforms, reducing the need for separate logins and enhancing security through centralized identity management.
Similarly, other frameworks like OAuth and LDAP offer reliable methods for managing user access, making OIDC a go-to solution for simplifying authentication while maintaining strict authorization control.