Table of Contents
In modern IT environments, securing networks is more challenging than ever. As organizations increasingly adopt complex infrastructures involving on-premises systems, cloud environments, and mobile users, traditional firewalls often fall short in providing adequate security and control.
Hybrid mesh firewalls have emerged as a solution, offering a layered and interconnected approach to protect these dynamic networks.
What Are Hybrid Mesh Firewalls?
Hybrid mesh firewalls combine multiple types of firewalls—network-based, host-based, and cloud-based—into a single, cohesive framework. This model integrates the strengths of each firewall type, creating a “mesh” of protection that spans the entire network.
A Hybrid Mesh Firewall will often include features such as stateful inspection, deep packet inspection, intrusion prevention systems (IPS), and application-layer filtering.
These firewalls are designed to work across hybrid environments, where some resources are hosted on-premises while others are in public or private clouds.
By unifying security policies and enforcement mechanisms, hybrid mesh firewalls enable organizations to maintain consistent protection regardless of where data resides or how it is accessed.
Core Components and Functionality
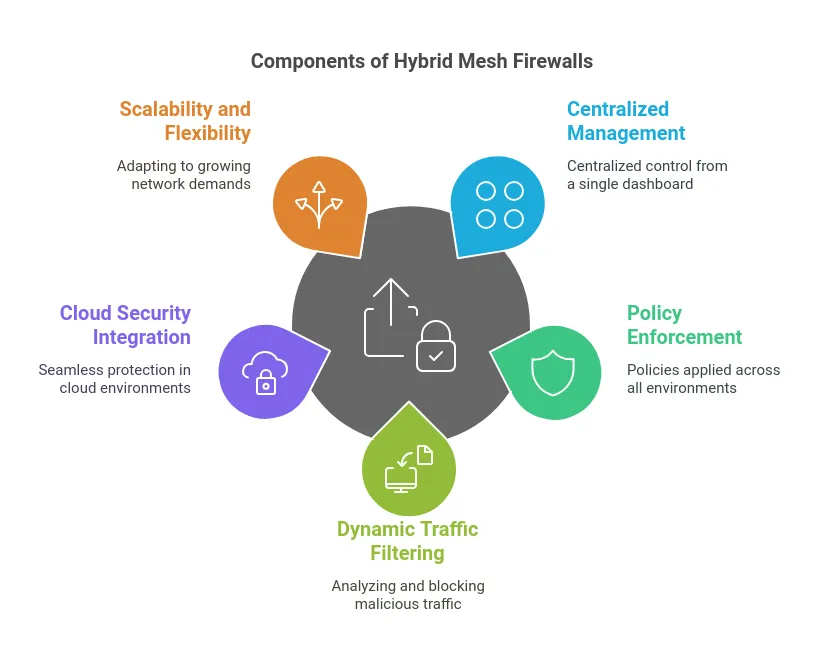
1. Centralized Management
A key feature of hybrid mesh firewalls is centralized management. Administrators can define and enforce security policies across all environments from a single dashboard. This approach reduces complexity, enhances visibility, and ensures uniform security measures.
2. Policy Enforcement Across Environments
Hybrid mesh firewalls enforce policies at multiple levels, including the perimeter, internal network, and endpoint devices. They ensure that sensitive data is accessible only by authorized users and applications, regardless of whether it is stored in an on-premises server or a cloud-based database.
3. Dynamic Traffic Filtering
These firewalls analyze traffic dynamically, applying stateful inspection and deep packet inspection to identify and block malicious activities. Advanced analytics and artificial intelligence are often integrated to detect sophisticated threats such as zero-day exploits.
4. Integration with Cloud Security
As organizations migrate to the cloud, hybrid mesh firewalls integrate with cloud-native security tools to provide seamless protection. They monitor traffic between on-premises and cloud environments, securing data flows while enabling secure access for remote users.
5. Scalability and Flexibility
Hybrid mesh firewalls are designed to scale with growing networks. They can accommodate increased traffic loads, additional users, and new applications without compromising security. This scalability is critical for organizations adopting microservices, containerized workloads, or multi-cloud architectures.
Why Are Hybrid Mesh Firewalls Important?
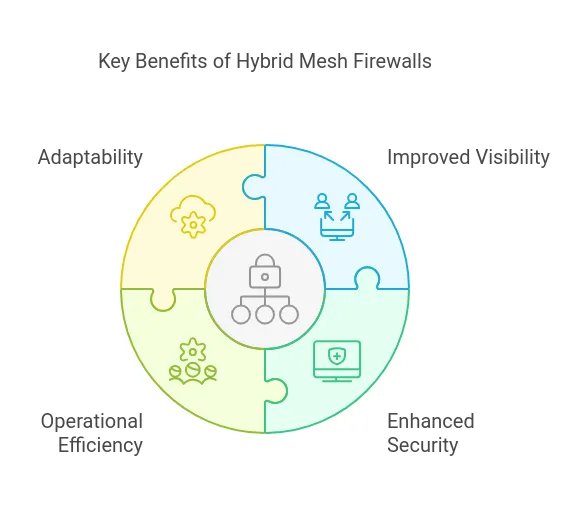
Hybrid mesh firewalls address the limitations of traditional firewalls, which often struggle to protect dispersed networks. They provide several key benefits:
- Improved Visibility: Unified logging and analytics give IT teams a comprehensive view of network activity.
- Enhanced Security: Advanced threat detection and prevention capabilities protect against emerging threats.
- Operational Efficiency: Centralized management reduces the administrative burden and minimizes the risk of configuration errors.
- Adaptability: These are well-suited for hybrid and multi-cloud environments, ensuring consistent security as infrastructure evolves.
Conclusion
Hybrid mesh firewalls are a cornerstone of modern IT security, providing the flexibility and resilience needed to protect complex, distributed networks.
By combining traditional and cloud-based firewall technologies into an integrated framework, they enable organizations to safeguard their data, applications, and users effectively, regardless of location.
As cyber threats continue to evolve, these will play a crucial role in maintaining secure, adaptive IT environments.
READ MORE:
Ground Breaking Power of AI-Driven Climate Models in Disaster Prevention
Distributed Systems: 6 Essential Steps to Scale Your Business Successfully