Table of Contents
Healthcare data breaches are happening more than ever. In 2024, 14 big breaches exposed over 1 million patient records each. The biggest breach affected 190 million people. Healthcare software development companies need strong security in their software to protect patient data and avoid big fines.
What Makes Medical Organisations Prime Targets for Cyberattacks?
Medical facilities store vast amounts of valuable patient data. This includes medical records, treatment histories, insurance details, and personal information. Medical systems cannot shut down during attacks without risking patient lives.
This vulnerability makes them attractive targets for cybercriminals. The numbers tell the story. The OCR data breach portal shows 725 breaches of 500+ records in 2024.
This marks the third consecutive year with over 700 large breaches. Statistics reveal that 30% of all major data breaches occur in hospitals compared to other industries.
Why Is Security-First Development Critical for Healthcare Software?
The global healthcare IT market was worth $420.23 billion in 2024. It will grow 14.7% yearly to reach $834.35 billion by 2029. This rapid growth increases cybersecurity risks.
Software development for healthcare must prioritise security from day one, not as an afterthought.
Based on our analysis of recent breaches, organisations that implement security-first development reduce their risk by up to 80%. This approach builds protection into every system component during the design phase.
What Are the Essential Security Features Every Medical Application Needs?
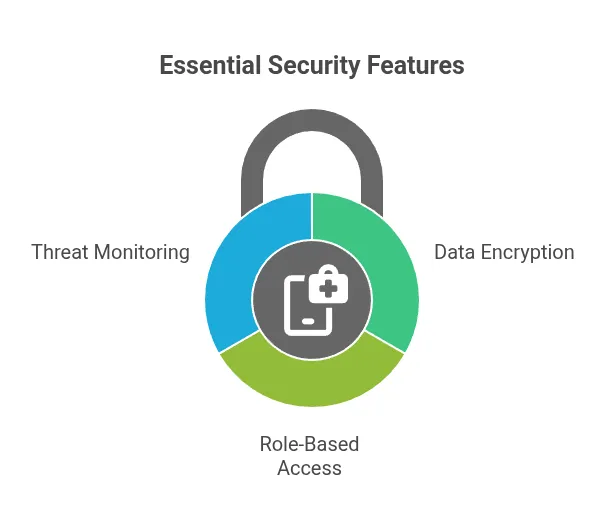
Data Encryption at Every Level
Strong encryption protects patient data during storage and transmission. Medical applications must use advanced encryption algorithms that make data unreadable to unauthorised users. Key management systems should control access to encrypted data through secure protocols.
Role-Based Access Controls
Modern healthcare systems limit data access based on job responsibilities. Nurses access different information than doctors or administrative staff.
Multi-factor authentication adds extra security layers by requiring users to verify their identity through multiple methods.
Real-Time Threat Monitoring
Security systems must track all user activities within Medical applications. These systems identify unusual patterns that might indicate threats.
Machine learning algorithms improve detection accuracy over time and can spot patterns humans might miss.
How Do Healthcare Organisations Ensure Regulatory Compliance?
In 2024, OCR closed 22 HIPAA investigations with financial penalties. This demonstrates increased regulatory enforcement.
Healthcare software development must meet strict compliance requirements from the start. HIPAA sets the standard for patient data protection in the United States.
Similar regulations exist worldwide to protect patient privacy. Developers use automated tools to check code against regulatory standards throughout the development process.
Key rules to follow:
- Keep data locked up when stored and sent
- Track who looks at patient data and when
- Check security often and fix problems
- Train staff on how to protect data
What Advanced Technologies Are Transforming Medical Security?
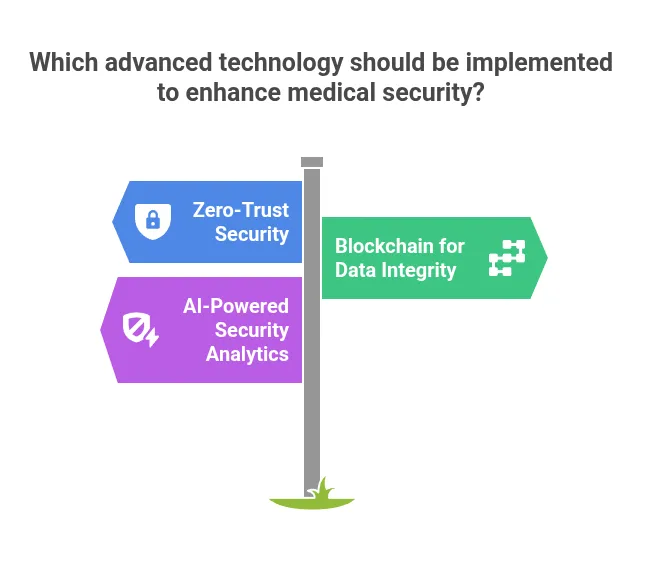
Zero-Trust Security Architecture
Zero-trust models assume no user or device is inherently trustworthy. Every access request requires verification regardless of location or credentials.
This approach reduces risks from internal threats and compromised accounts.
Blockchain for Data Integrity
Blockchain technology creates tamper-proof records of patient data changes. Each modification creates a permanent, verifiable entry.
Medical applications use blockchain to maintain transparent audit trails while protecting patient privacy.
AI-Powered Security Analytics
Artificial intelligence analyses vast amounts of security data to identify emerging threats. These systems detect subtle patterns and predict potential vulnerabilities.
Predictive analytics helps prevent security incidents before they occur.
How Can Healthcare Organisations Build Resilient Systems?
Between January and September 2024, US healthcare organisations experienced 491 large-scale data breaches.
Each resulted in the loss of over 500 records. Effective software development for healthcare includes comprehensive disaster recovery planning.
Key ways to stay strong:
- Keep extra copies of data in safe places
- Test systems often to find weak spots
- Make clear plans for when attacks happen
- Teach staff how to handle security issues
What Role Does Cloud Computing Play in Healthcare Security?
The healthcare cloud computing sector was worth over $40 billion in 2024. Cloud providers invest heavily in security infrastructure that individual organisations cannot afford.
However, medical organisations must carefully evaluate cloud security controls. Cloud-native security solutions offer scalability and flexibility while maintaining strict medical standards. Organizations should implement proper cloud security configurations and regular monitoring.
How Do You Measure Healthcare Security Program Success?
Nearly 43.38% of health data was compromised from 2005 to 2019, the highest among all sectors. Medical organizations need clear metrics to evaluate their security programs.
Key things to measure:
- How fast do you fix security problems
- How quickly you patch weak spots
- Your scores on safety checks
- How many staff members finish security training
Third-party security assessments provide an objective evaluation of security measures. Patient feedback also offers insights into security program effectiveness and trust levels.
Key Takeaways for Healthcare Security Success
Securing patient data requires a comprehensive approach that balances security, usability, and compliance. Organizations must implement multiple protection layers while maintaining system performance.
Summary of key steps:
- Build security into software from the start
- Use strong encryption to protect data
- Set up smart threat detection tools
- Follow all rules and laws
- Create backup plans for emergencies
- Track and improve your security program
Good security protects patient data and your reputation. Healthcare companies with strong security earn more trust from patients. New technology will bring new risks. Start building strong security today to stay safe tomorrow.
FAQs
Q1. Why are healthcare organizations prime targets for cyberattacks?
Healthcare organizations are appealing targets because they store vast amounts of valuable patient data, including medical records and personal information. Their inability to shut down systems during an attack due to the necessity of continuing patient care makes them particularly vulnerable.
Q2. What is security-first development, and why is it important for medical software?
Security-first development prioritizes security measures from the initial stages of software design, rather than treating it as an afterthought. This approach significantly reduces the risk of data breaches—by up to 80%—by building protection into every component of the software.
Q3. What essential security features should healthcare applications include?
Key security features for healthcare applications include:
– Data Encryption: Protecting data during storage and transmission using advanced encryption algorithms.
– Role-Based Access Controls: Limiting data access based on the user’s job responsibilities, enhanced by multi-factor authentication.
– Real-Time Threat Monitoring: Employing systems to track user activities and detect unusual patterns indicative of potential threats.
Q4. How do healthcare organizations ensure regulatory compliance?
Medical software development must adhere to strict compliance requirements from the start, particularly with regulations like HIPAA. Organizations utilize automated tools to check their code against these standards, ensuring proper data handling, access tracking, and security checks.
Q5. What advanced technologies are being used to enhance healthcare security?
The integration of advanced technologies such as Zero-Trust Security Architecture, which requires verification for every access request, and blockchain technology, which maintains tamper-proof records of data changes, is transforming healthcare security. Additionally, AI-powered security analytics help in identifying and predicting potential threats by analyzing vast amounts of security data.