Table of Contents
The world stands at the brink of a quantum computing revolution, a technological leap that promises unparalleled computational power. While quantum computers hold the potential to solve problems once considered unsolvable, they also pose a grave threat to the cryptographic systems that secure the digital world.
Post-quantum cryptography (PQC) emerges as a vital defense mechanism. It represents a new class of cryptographic techniques specifically designed to remain secure even in the face of quantum computing’s vast capabilities.
Understanding the Quantum Threat
The Nature of the Quantum Threat
Quantum computers operate on fundamentally different principles than classical computers. By leveraging quantum mechanics, they can process and analyze data in ways that were once theoretical. For example:
- Superposition: This principle enables quantum bits (qubits) to exist in multiple states at once, facilitating parallel computations and enhancing processing power.
- Entanglement: Links qubits in ways that make their states interdependent, allowing for the rapid propagation of information.
These properties enable quantum computers to solve specific mathematical problems exponentially faster than classical machines. For instance, Shor’s algorithm—a quantum algorithm—can efficiently factorize large numbers, rendering RSA encryption vulnerable. Similarly, Grover’s algorithm speeds up the brute-force attacks on symmetric key systems like AES.

Quantum Threat Timeline
Although large-scale quantum computers capable of breaking today’s cryptography are still in development, rapid progress suggests that this threat could materialize within the next decade or two. Governments and enterprises must act now to secure sensitive information that may still be valuable decades into the future.
The Need for Enhanced Security
The increasing reliance on digital systems for communication, commerce, healthcare, and defense makes data security paramount. Traditional cryptographic algorithms, while robust against classical attacks, are ill-equipped to handle quantum-enabled breaches. Post-quantum cryptography addresses this gap by introducing algorithms resistant to both classical and quantum attacks, ensuring the longevity and reliability of secure systems.
What is Post-Quantum Cryptography?
Post-quantum cryptography refers to cryptographic systems explicitly designed to withstand quantum computer attacks. Unlike quantum cryptography, which uses quantum mechanics for secure communication (e.g., quantum key distribution), PQC operates within classical computational frameworks. It focuses on creating mathematically complex problems that quantum computers cannot solve efficiently.
The Rise of Quantum Computing and Its Impact on Post-Quantum Cryptography
Breakthroughs in Quantum Technology
Quantum computing has transitioned from a theoretical concept to a practical reality, reshaping the technological landscape. This revolution has been marked by several groundbreaking milestones:
- Google’s Quantum Supremacy: In a landmark achievement, Google’s quantum computer solved a problem in mere seconds that would take classical supercomputers thousands of years to process.
- Scalable Quantum Processors: Tech giants like IBM are spearheading the development of scalable quantum processors, aiming to bring quantum computing closer to mainstream adoption.
- Government Investments: Across the globe, governments are investing billions of dollars in quantum research to secure leadership in this transformative technology.
Potential Implications for Encryption
The rise of quantum computing poses a severe threat to traditional cryptographic methods. Algorithms like RSA and ECC, which secure digital communications today, rely on mathematical problems that quantum computers can solve exponentially faster than classical computers. This capability could enable:
- Decryption of Sensitive Data: Breaking encrypted data, such as financial transactions and personal communications, exposing it to malicious actors.
- Forgery of Digital Signatures: Quantum computers can forge cryptographic signatures, compromising authentication mechanisms.
- Identity Impersonation: Threat actors could impersonate legitimate entities, jeopardizing trust in digital systems.
Post-quantum cryptography (PQC) emerges as a robust countermeasure, offering algorithms designed to resist both classical and quantum attacks.
Key Concepts of Post-Quantum Cryptography
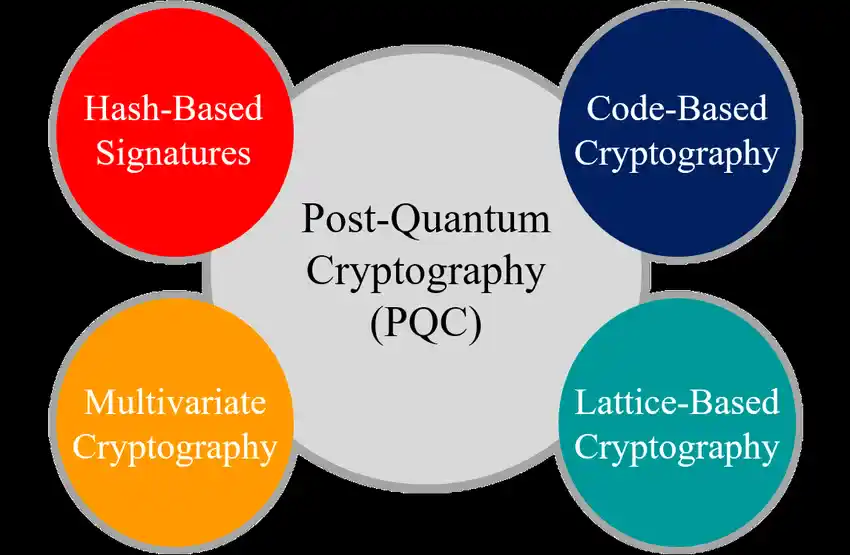
Post-quantum cryptography builds on mathematical problems that are computationally infeasible for quantum computers to solve. Three prominent approaches include:
- Lattice-Based Cryptography: Lattice-based cryptography focuses on high-dimensional lattice problems, such as the Learning With Errors (LWE) problem. These problems are resistant to quantum attacks due to their inherent computational complexity. This approach is a leading candidate for post-quantum encryption and key exchange protocols.
- Hash-Based Signatures: Hash-based cryptographic systems utilize secure hash functions to create robust digital signatures. They are extensively studied and offer a reliable, quantum-resistant solution for validating digital identities and securing communications.
- Multivariate Polynomial Cryptography: This method uses systems of nonlinear polynomial equations over finite fields, creating encryption schemes that remain secure even against quantum computational power.
Benefits of Post-Quantum Cryptography
Adopting post-quantum cryptography offers several key advantages:
- Future-Proof Security Solutions: PQC anticipates the challenges posed by quantum computing, ensuring that sensitive data remains protected against emerging quantum threats. It provides long-term security for information that could otherwise be exposed decades into the future.
- Compatibility with Existing Systems: Many PQC algorithms are designed to integrate seamlessly with current infrastructure, allowing organizations to enhance their security without the need for complete system overhauls.
- Building Trust in Digital Transactions: In an increasingly digital world, PQC strengthens the foundation of trust by ensuring secure communications, financial transactions, and e-commerce.
Challenges in Implementing Post-Quantum Cryptography
Despite its benefits, post-quantum cryptography faces several hurdles:
- Standardization Efforts: Global initiatives, such as the NIST Post-Quantum Cryptography Standardization Project, aim to identify and standardize the most secure and efficient PQC algorithms. However, the process is complex and requires consensus across various stakeholders.
- Performance and Efficiency: PQC algorithms often demand larger key sizes and greater computational resources than classical cryptographic methods. This can strain resource-constrained devices like IoT gadgets and mobile systems.
- Integration with Legacy Systems: Transitioning to PQC requires updating existing infrastructure to accommodate new cryptographic standards while maintaining compatibility with legacy systems. This process can be time-consuming and resource-intensive.
The Future of Post-Quantum Cryptography
- Ongoing Research and Development: Post-quantum cryptography is an active area of research, with experts refining algorithms to enhance their security, efficiency, and scalability. Continued innovation will be key to addressing emerging quantum threats.
- Collaborative Global Efforts: The transition to PQC requires cooperation among governments, academia, and industry to standardize, implement, and promote these cryptographic systems. Collaborative efforts are crucial for building a secure global ecosystem.
- Preparing for a Quantum-Driven World: Organizations must proactively adopt PQC to ensure resilience against quantum threats. Early implementation will safeguard critical data and systems, providing a secure foundation for the quantum era.
Conclusion
Post-quantum cryptography represents a paradigm shift in securing the digital world. By addressing vulnerabilities posed by the advent of quantum computing, PQC ensures the long-term security of data, systems, and communications. As quantum computing progresses, the urgency to adopt PQC becomes increasingly evident.
Governments, enterprises, and individuals must prioritize this transition to safeguard the future of digital trust, privacy, and security. In a quantum-driven world, post-quantum cryptography will be indispensable for maintaining a secure and reliable digital ecosystem.
READ MORE:
IT Services Expansion: Breaking Borders for Global Success
7 Healthcare Trends in Technology Poised to Revolutionize Medicine in 2025