Table of Contents
Web application development has become a prerequisite for industries to function properly in today’s world as every aspect of running, communicating or transacting a business is service-oriented and digitally enabled. However, with the rise of technology, cybersecurity threats have emerged. Implementing solid web security applications is imperative to protect trust and business continuity.
Understanding Cybersecurity for Web Applications
With the evolution of technology and particularly the rapid increase in internet usage, no business is free from vulnerabilities. Web applications are particularly prone to cyber intrusive activities due to their open and exposed nature. Weaknesses range from user data theft, application unavailability, and business interruption which can lead to drastic consequences.
Common Threats to Web Applications
- SQL Injection (SQLi): this type of threat targets databases and takes advantage of insecure design (malicious web pages) to obtain databases without permission
- Cross-Site Scripting (XSS): in simpler terms, this exploit allows entry of harmful and unsafe code into web pages which can lead to data stealing from users
- Cross-Site Request Forgery (CSRF): a user’s trust towards particular websites is abused for carrying out undesirable tasks
- Distributed Denial of Service (DDoS): the denial of service attack floods the servers with heavy traffic which causes the application to stop functioning
- Man-in-the-Middle (MitM) Attack: Using this form of attack, users of the application can intercept messages exchanged within the application.
This highlights some of the many risks and vulnerabilities that web applications penetrate if not protected. Implementing protection against these threats is how the concept of security for web services was born.
Best Practices for Building Secure Web Applications
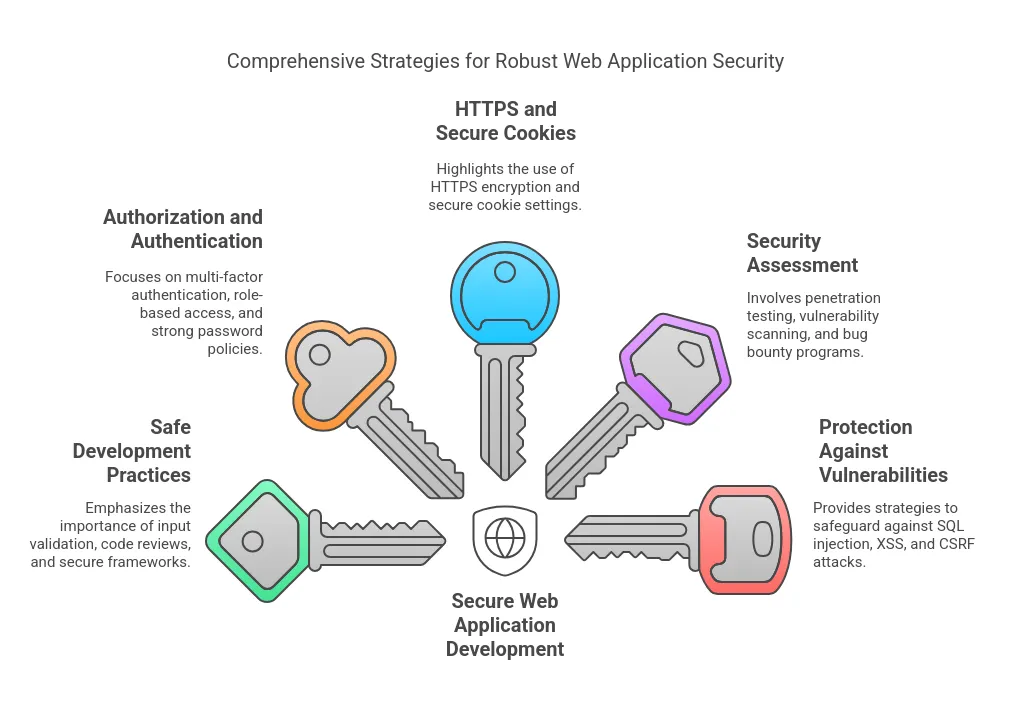
1. Integrate Safe Procedures During The Development Stage
- Input Validation: Every data supplied by users must be authenticated and cleansed to refrain from processing any harmful data.
- Code Reviews: Regularly conduct scans on the code so that no risks are skipped.
- Secure Frameworks: Choose frameworks that offer Inherent protection, for example, Django and Ruby on Rails.
2. Employ Authorization and Strong Authentication
- Multi-Factor Authentication (MFA): Using a combination of different methods to authenticate a user’s access instead of relying solely on passwords adds another protective layer.
- Role-Based Access Control (RBAC): To limit usage of critical areas, access rights should be given according to assigned user classifications.
- Password Policies: Promote the practice of selecting passwords that are hard to guess and one of a kind, and implement robust hashing algorithms such as bcrypt for the safe saving of passwords.
3. Make Use of HTTPS And Cookies With Security
- HTTPS Encryption: Information online being sent should be protected by using SSL/TLS certificates.
- Secure Cookies: Specify cookies to be marked as safe and HttpOnly to limit the chances of theft and manipulation.
4. Systematic Security Assessing
- Penetration Testing: Attack system intentionally to check for weaknesses adversaries may take advantage of.
- Vulnerability Scanning: Automated scans with a dast software on expired managed libraries and intangible configurations.
- Bug Bounty Programs: Ethnic hackers are motivated to find and report on security weaknesses.
5. Safeguard Against Frequently Exploited Vulnerabilities
- SQL Injection Protection: Use parameterized queries and prepared statements.
- XSS Protection: Implement Content Security Policy (CSP) headers and encode output.
- CSRF Tokens: Use anti-CSRF tokens to verify the authenticity of requests.
6. Activity Tracking and Supervision
- Activity Logs: Record users’ actions and system events to find unusual patterns.
- Intrusion Detection Systems (IDS): Determine and act on possible threats.
- Alert Mechanism: Immediately inform administrators of potentially harmful behaviours.
Enhancing Security with VPNs
Virtual Private Networks (VPNs) are an essential tool in securing web applications. They encrypt internet traffic, ensuring safe communication between users and web platforms while safeguarding sensitive data from interception. To simplify the process, cybersecurity experts at Cybernews have crafted a detailed Surfshark VPN review for you to explore. This review highlights Surfshark’s capabilities in enhancing privacy and security, making it a strong candidate for integrating VPN solutions.
Employing third-party Applications and Services
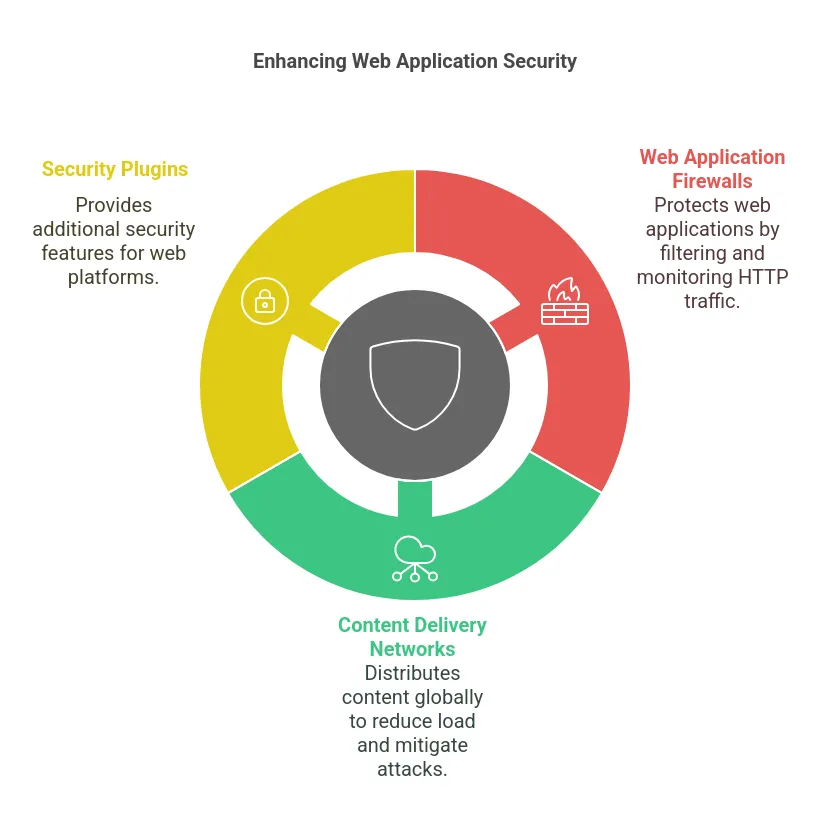
The use of selected third-party applications and services can significantly improve protection for web applications:
- Web Application Firewalls (WAF): Monitor and prevent harmful traffic.
- Content Delivery Networks (CDNs): Reduce the impact of DDoS attacks and enhance application speed.
- Security Plugins: Plugins such as Wordfence for WordPress and the rest of the platforms offer similar features.
Training the Teams and the Users
A secure online platform cannot exist by just focusing on technology, there also have to be people:
- Developers Training: Developers must know secure coding.
- User Training: Users need to be trained on phishing, password, and safe sites.
- Updates: Inform teams about emerging security awareness tips.
Educating on the Current Security Trends
Constantly, the world of cybersecurity keeps changing. Therefore, organizations are required to:
- Threat Intelligence Monitoring: New threats and weaknesses should be tracked.
- Patching: Updates and patches should be done as often as possible and vulnerabilities fixed.
- Community Participation: Knowledge sharing and receiving should take place in security forums and their communities.
Conclusion
Building secure web applications requires a multi-layered approach combining technology, practices, and education. By understanding threats, implementing defences, and fostering security awareness, organizations can safeguard platforms and protect users’ data. Tools like VPNs, as highlighted in the Surfshark VPN review by Cybernews, add an extra layer of resilience. Cybersecurity is a continuous commitment that ensures trust and excellence in a data-driven digital world.